OSINT and Social Engineering Challenges Write-Up:
Osint-challenge-6: Only time will tell!
| DESCRIPTION
This picture was taken sent to us! It seems like a bomb threat! Are you able to tell where and when this photo was taken? This will help the investigating officers to narrow down their search! All we can tell is that it’s taken during the day! If you think that it’s 7.24pm in which the photo was taken. Please take the associated 2 hour block. This will be 1900-2100. If you think it is 10.11am, it will be 1000-1200. Flag Example: govtech-csg{1.401146_103.927020_1990:12:30_2000-2200} Use this calculator! Flag Format: govtech-csg{lat_long_date_[two hour block format]} Addendum: – The amount of decimal places required is the same as shown in the example given. – CLI tool to get something before you convert it with the calculator. |

For this challenge, it was necessary to submit a flag containing the GPS latitude and longitude given in the above picture, as well as the date and time that the picture was taken, in the following format: govtech-csg{lat_long_date_[two hour time]}
From a cursory glance, the picture has not had EXIF data scrubbed. Perfect!
We make use of the tool exiftool to gather more information about the file and translate the latitude and longitude into a usable format:
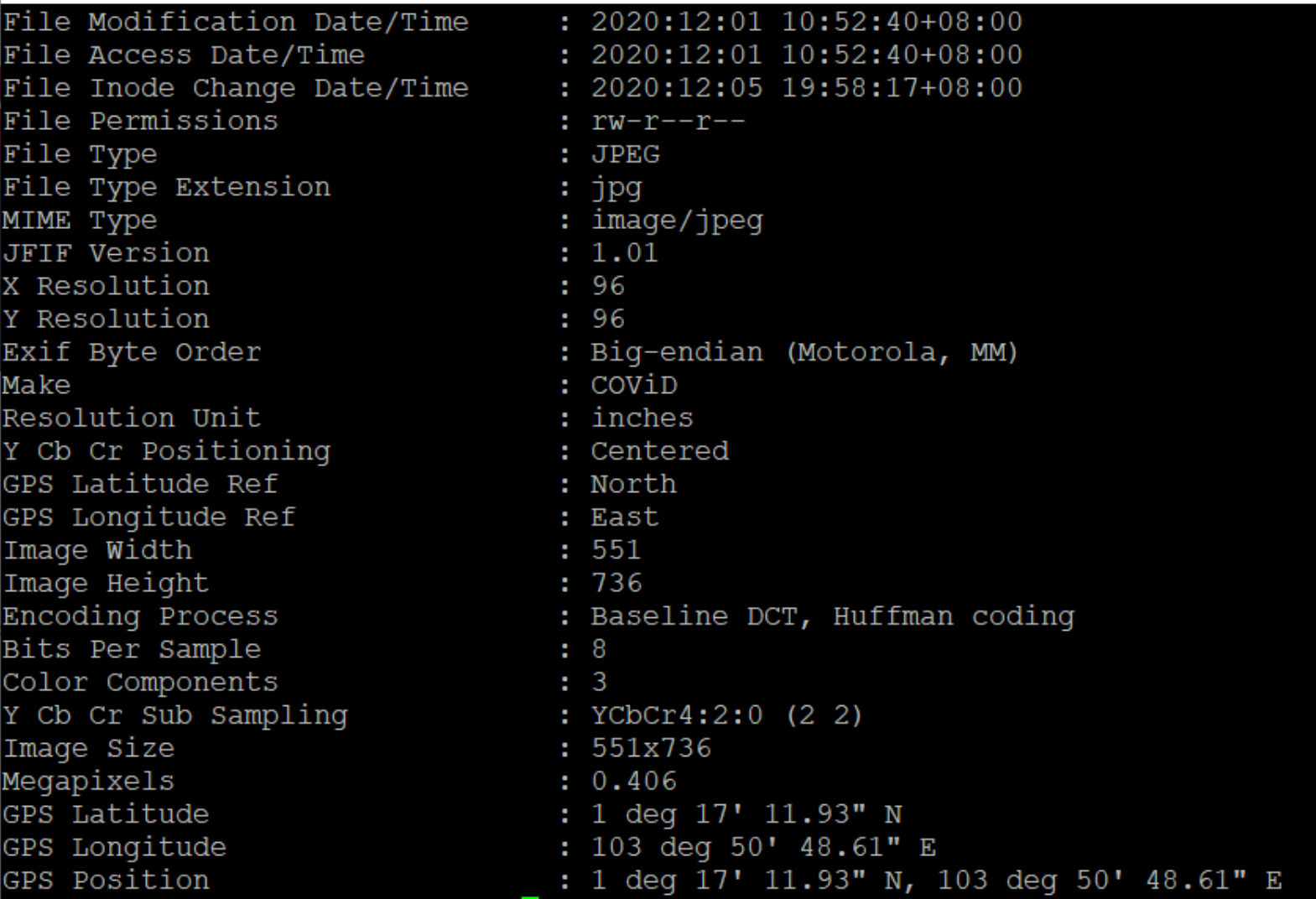
From here, we can input the last two lines of the GPS latitude and longitude into the provided calculator to get the latitude and longitude into the format required by the flag:
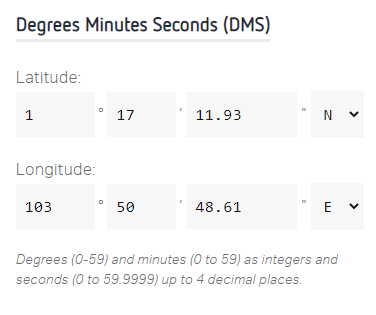
The output of the decimal degrees provided by the tool are part of the flag with X: 103.846836, Y: 1.286647.

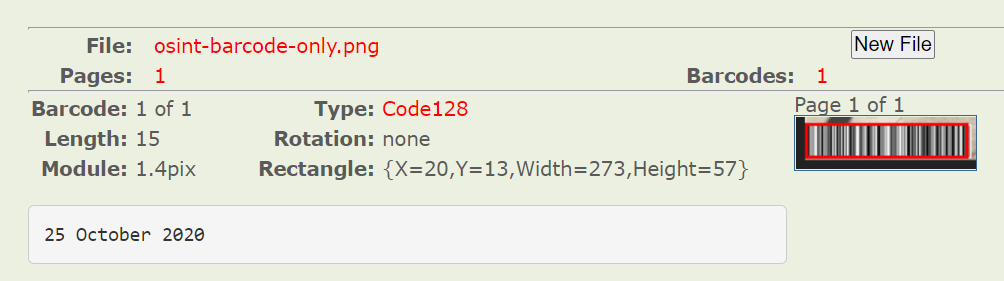
Next, we notice that there is a barcode encoded in code-128 in the bottom left of the image. Perhaps scanning this could give us more information. We can scan the barcode with this online tool, and derive the date the picture was taken from it.
Lastly, we must get the approximate time the photo was taken in two-hour blocks. While it is possible to use complex calculations [i.e. through seeing the position of the shadows cast by objects] using suncalc (a write-up where an author did this in a previous CTF challenge is available here), as they had lifted the submission limits for this challenge, we can simply guess the two-hour blocks in order of likelihood until we get the correct time. As the sun appears to be bright in the sky and the shadows cast are not “very straight” (indication of high noon), that would indicate that it was in the later part of the day, but before the evening time period.
Flag: govtech-csg{103.846836_1.286647_2020:10:25_1500-1700}
Osint-challenge-2: What is he working on? Some high value project?
| DESCRIPTION
The lead Smart Nation engineer is missing! He has not responded to our calls for 3 days and is suspected to be kidnapped! Can you find out some of the projects he has been working on? Perhaps this will give us some insights on why he was kidnapped…maybe some high-value projects! This is one of the latest work, maybe it serves as a good starting point to start hunting. Flag is the repository name! Developer’s Portal – STACK the Flags Note: Just this page only! Only stack-the-flags-2020 page have the clues to help you proceed. Please do not perform any scanning activities on www.developer.tech.gov.sg. This is not part of the challenge scope!” |
This challenge is a little more straightforward than the previous one. Visiting the provided link yields a page with some descriptions on it. Hmm… maybe there is information here that is not visible on the page. On line 858 of the linked web page, we see the following HTML comment:
| <!– Will fork to our gitlab – @joshhky –> |
Interesting. Perhaps this is related to the engineer that is working on the project. Since we have his handle, we can look at his GitLab page, which yields some projects and repositories. On the korovax-employee-wiki repository, the README yields another line on the todo:
| eg, Josh will be in charge of the krs-admin-portal – Please note that not all repository should be made public, relevant ones with business data should be made private |
Perhaps krs-admin-portal is the name of the high-value project he is working on? If we try to format it into the required format, we find that it is indeed the project and the flag.
Flag: govtech-csg{krs-admin-portal}
Osint-challenge-3: Where was he kidnapped?
Challenge Description:
| DESCRIPTION
The missing engineer stores his videos from his phone in his private cloud servers. We managed to get hold of these videos and we will need your help to trace back the route taken he took before going missing and identify where he was potentially kidnapped! You only have limited number of flag submissions! Flag Format: govtech-csg{postal_code} |
This was an interesting challenge in which the engineer was kidnapped in broad daylight, but we have the three videos as shown above. In the first video, we are shown that the bus he was waiting for is service 117, in the direction of Punggol Interchange.

Next, he appears to alight near a public housing development and laments that it is not near an MRT [train] station.

The final video shows that he is at the void deck of one of the public housing blocks with some seating space, a table and a garden behind it, before he appears to get kidnapped.

We can start off by identifying where he alighted from the bus, which should provide some indication of the surrounding where he was kidnapped. Conveniently, TransitLink does provide an electronic guide for bus services. We are only interested in “Direction 2”, since that is in the direction of Punggol Interchange. From here, we can narrow it down to only public housing estates which the bus service calls at.
We then take to Google Maps to look at some of the possible stops that may match the second picture. At the bus stop for Blk 871 Yishun Ave 1, we see a walkway that looks suspiciously similar to the one in the second picture.

Perhaps he was abducted in one of the nearby blocks? Let’s investigate by taking to StreetView of the carpark that serves this set of housing blocks. From here, we do spot the location that appears to be where the developer was when he was kidnapped.

We can see the block number on a nearby display and get it’s address from Google Maps: 
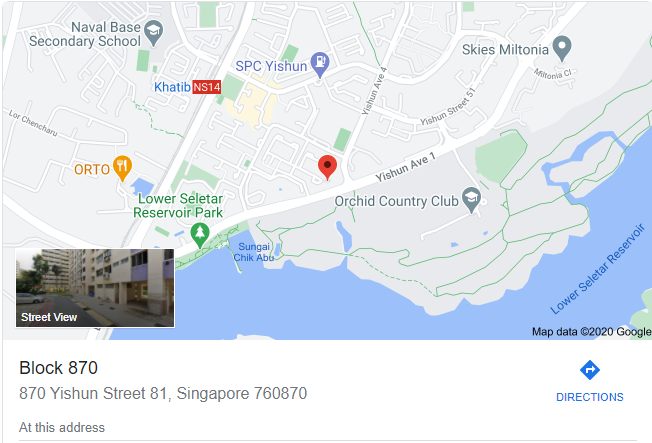
Flag: govtech-csg{760870}
Osint-challenge-7: Sounds of freedom!
| DESCRIPTION
In a recent raid on a suspected COViD hideout, we found this video in a thumbdrive on-site. We are not sure what this video signifies but we suspect COViD’s henchmen might be surveying a potential target site for a biological bomb. We believe that the attack may happen soon. We need your help to identify the water body in this video! This will be a starting point for us to do an area sweep of the vicinity! Flag Format: govtech-csg{postal_code} |
This challenge involved another video file that was taken, presumably from a high-rise flat that shows a bus stop of a certain design, before panning up to reveal what appears to be a park and a water body that appears to be green.


Therefore, we have a few criterias that we can set out to narrow down the list of locations that we have to fulfil:
– Has to have a highrise building, with a bus stop on the opposite side of the road
– Bus stop has to be in front of a park or similar amenity with a water body
– Water would probably appear to be green
Fortunately, based on Google Maps, there aren’t that many water bodies in Singapore with residential housing that overlooks it and we can narrow down our search to a few locations.
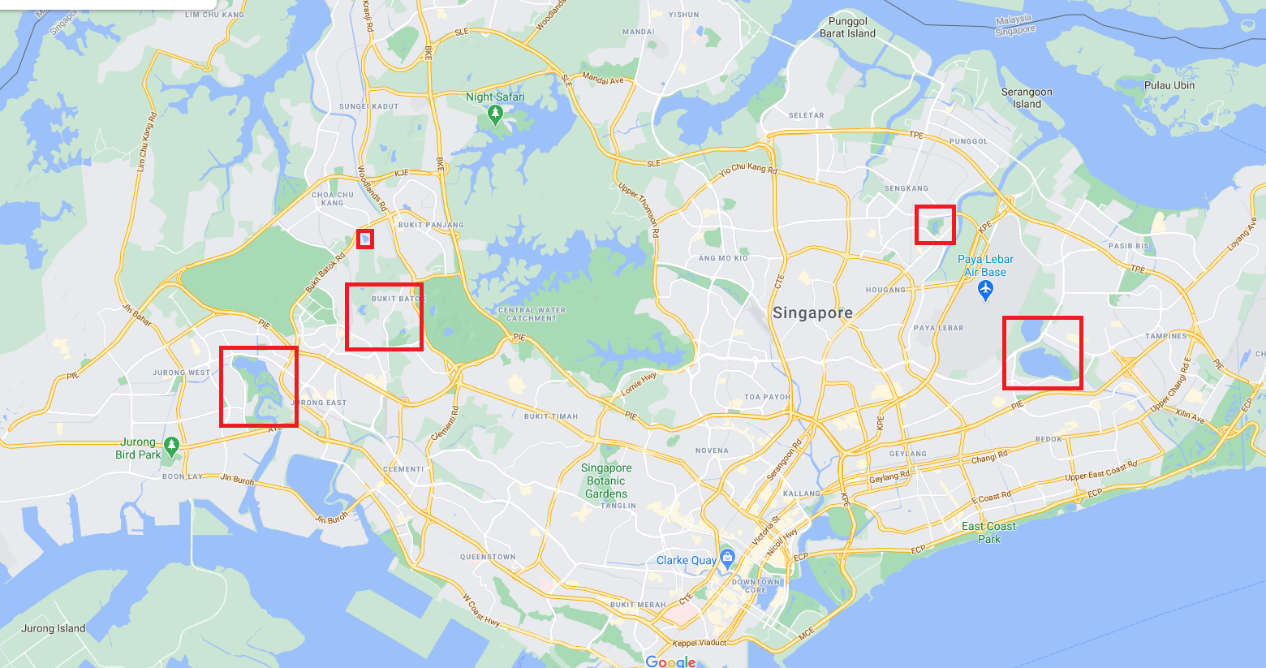
From here, we can iterate through them. Upon looking into the water body in the north-east on Google Streetview, we make an discovery:

From the background of the bus stop, to the water body behind it that looks slightly green, this does appear to be the place where the bomb could be planted. The name of the park behind this bus stop is “Punggol Park”, and as the flag requires the postal code of the park, we can just Google the postal code.
Flag: govtech-csg{538768}
Osint-challenge-8: Hunt him down!
| DESCRIPTION
After solving the past two incidents, COViD sent a death threat via email today. Can you help us investigate the origins of the email and identify the suspect that is working for COViD? We will need as much information as possible so that we can perform our arrest! Example Flag: govtech-csg{JohnLeeHaoHao-123456789-888888} Flag Format: govtech-csg{fullname-phone number[9digits]-residential postal code[6digits]} |
There is an email for us to analyse here. Hmm…
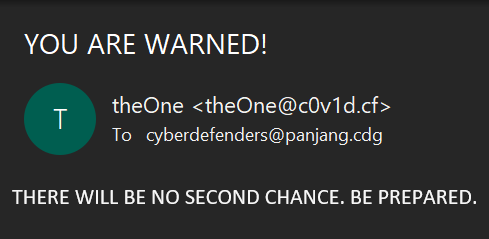
In an ideal scenario, there would be more information available in the mail headers that may reveal more information about the sender, but unfortunately in this case the mail headers don’t really reveal much more information and we only have the domain c0v1d.cf.
Firstly, we check whether the domain is existent by checking dig for the NS records and WHOIS. This is because some domains may not have DNS records set up, or the TLD of the domain may not have WHOIS properly setup.
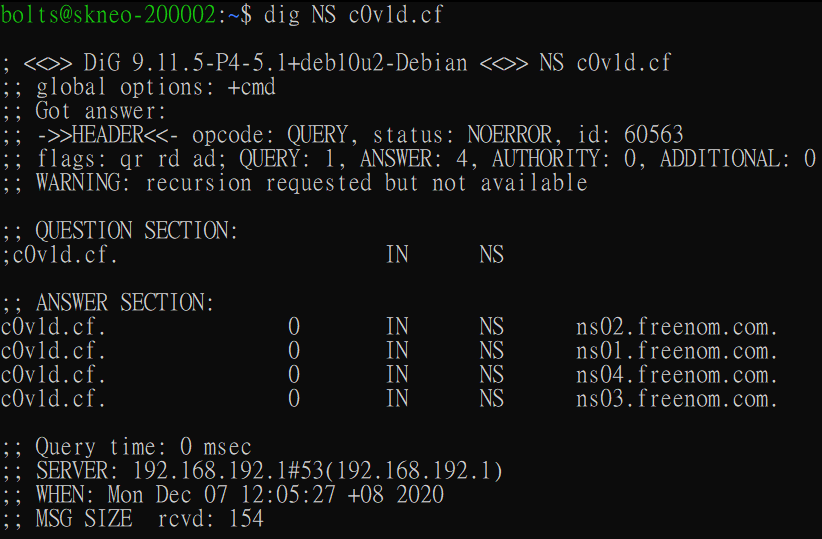
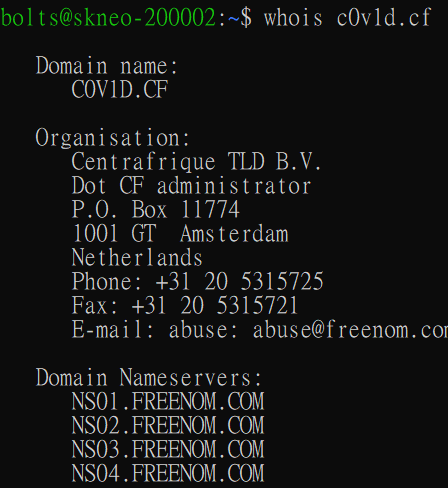
In this case, we see that the domain IS indeed registered and has a working DNS setup, although we cannot get the registrant information from this WHOIS check.
Since there are different types of DNS records, perhaps sometimes these could yield more information?
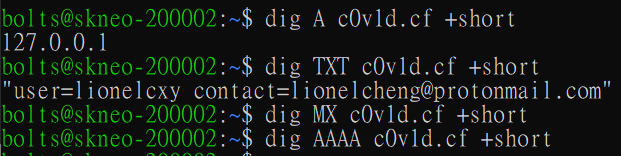
Aha. The TXT record for this domain does yield some additional information, about a user called “lionelcxy”. Perhaps we can do some searching based on this user identifier. Doing a cursory Google search reveals LinkedIn, Instagram and Carousell profiles for this person.
He has his full name shown on LinkedIn, so that was slightly more straight forward.
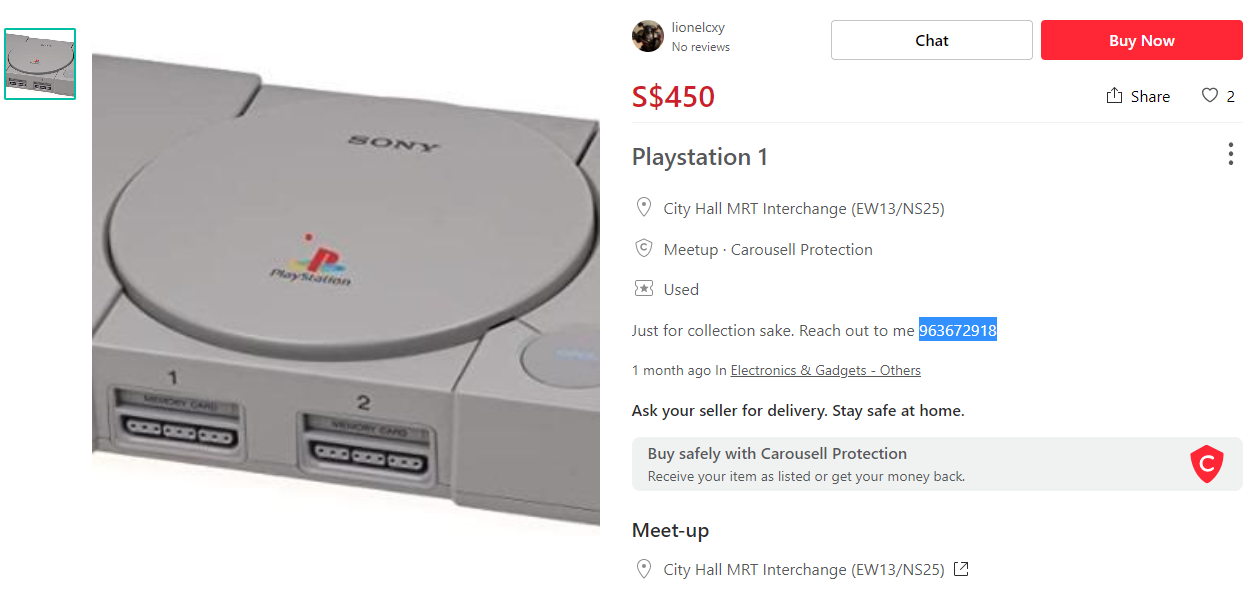
Next, maybe he would reveal his phone number on Carousell if he has any listings so people can contact him more easily? On his Carousell page, he has a listing for an original PlayStation and his phone number is here as well.
Lastly, finding a residential address is not as easy. From his Instagram profile, he says that the food street “Lau Pa Sat” Is “Just minutes away”, and links to his Strava workouts tracking account. Here, we see two activities on the same day – presumably where he started at One Fullerton to Marina Bay Sands and one for his return journey, but he took a detour. However, there don’t appear to be any residential properties near One Fullerton. On his return journey, however, he does make the following comment “Wanted to get home, but I can’t win my tummy!
Social Space closes so early. It was just at my block…”
Hmm… Social Space may be the name of a location, and from a cursory look, we can see that it is a café with two outlets – one near Outram Park and another at Marina One. Presumably, he is talking about the Marina One outlet “at my block”. This is probably the location where he lives. We can get the postal code of this outlet by Googling.
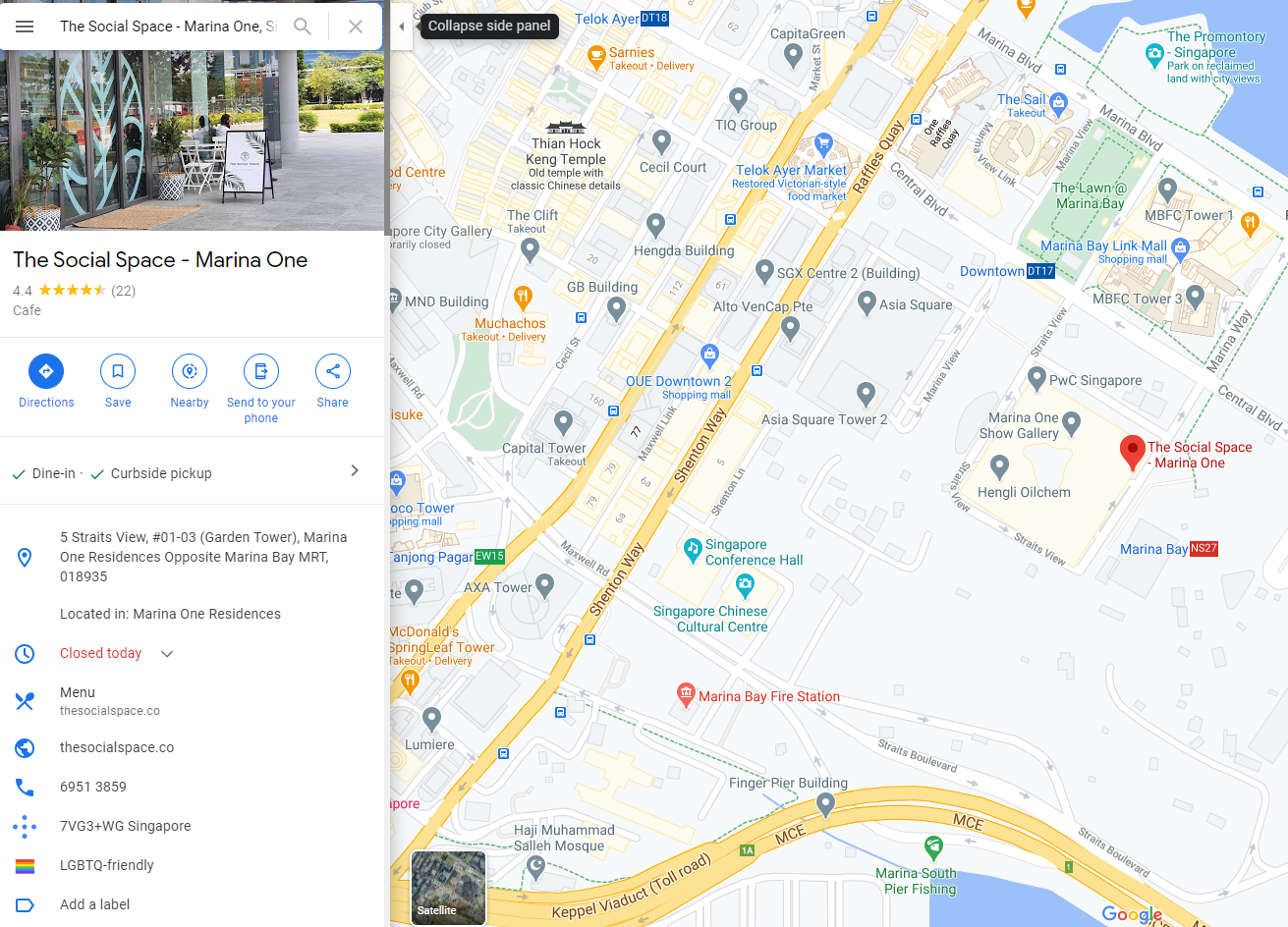
Now, we can put the pieces together to assemble our flag:
Flag: govtech-csg{LionelChengXiangYi-963672918-018935}
Osint-challenge-3: Who are the possible kidnappers?
| DESCRIPTION
Perform OSINT to gather information on the organisation’s online presence. Start by identifying a related employee and obtain more information. Information are often posted online to build the organization’s or the individual’s online presence (i.e. blog post). Flag format is the name of the employee and the credentials, separated by an underscore. For example, the name is Tina Lee and the credentials is MyPassword is s3cure. The flag will be govtech-csg{TinaLee_MyPassword is s3cure} Addendum: – Look through the content! Have you looked through ALL the pages? If you believe that you have all the information required, take a step back and analyse what you have. – In Red Team operations, it is common for Red Team operators to target the human element of an organisation. Social medias such as “Twitter” often have information which Red Team operators can use to pivot into the organisation. Also, there might be hidden portal(s) that can be discovered through “sitemap(s)”? I guess if you can log in with the password, then you should look at the flag format again! Note: engaging/contacting Ms. Miller is not in scope for this ctf. |
At this point, we have some information on the organisation – that it’s name is Korovax, and that Josh was presumably one of the employees of this organisation. We can do a Google search for “Korovax” to find the company’s web site. As this is a WordPress blog-website, we can get a list of the pages on the website (called a sitemap), some of which may not normally be visible, that could give more information. We find one such page “Oh Ho!”, where it details that they have their own internal social media website, that looks suspiciously like Facebook. Hmm… It also says that the user had forgotten their password to this site with “…blue…something….communication…”
Unfortunately, we have to identify the user before we can get more information supposedly.
From the Team page, we see three employees, with Sarah Miller being listed as one of them. The challenge description also states that engaging/contacting her is not in scope. Interesting. Let’s investigate this person further. We find that she has a Twitter handle @scba (the “REAL Sarah Miller”!) via the blog post on the website on Phase 3 Efficacy Trial.
Ordinarily, we might brush this off as placeholder text for a CTF-type competition, but maybe there could be some information we can derive from her profile. We had heard that it was “blue <something> communication”, perhaps this is a search we could do.
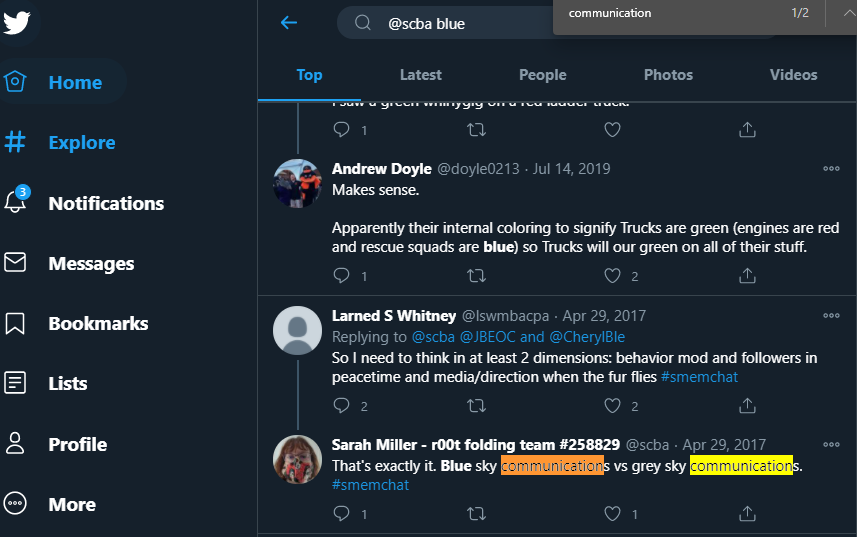
We find the relevant tweet and it is “Blue sky communications”. Since there is the internal social media site, and we have her email sarah.miller@korovax.org from the Teams website, we could try these credentials there.
A word of caution: Searching “communication” may not yield any results with the above search term. Note that Twitter only loads a few tweets on page load. In addition, Twitter only renders certain parts of the page that changes as the page scrolls (maybe for memory reasons?), so searching may not yield any results if that part is not being rendered in the browser. A better tool would perhaps have been a tweet searcher that goes through all of an account’s old tweets.
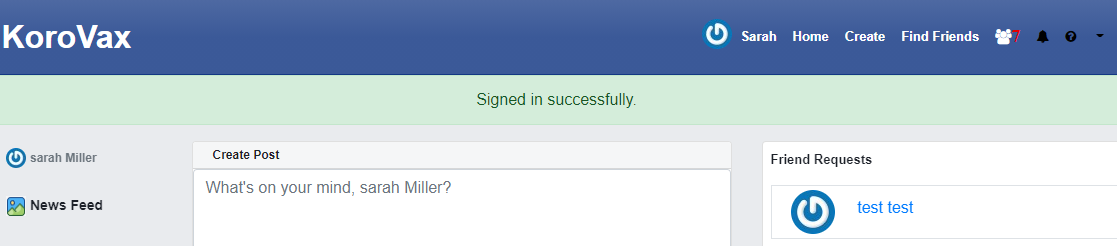
Success! It looks like Sarah Miller is somewhat related to our target after all. We can thus, form the flag from here:
Flag: govtech-csg{SarahMiller_Blue sky communications}
Se-challenge-1: Can you trick OrgX into giving away their credentials?
| DESCRIPTION
With the information gathered, figure out who has access to the key and contact the person. |
We need more information on how to contact the person. From the Korovax website, one of the blog posts is that there was an automated service desk that can help Korovax employees deal with technical issues. Additionally, we can make an account on their internal social media site to look at some of the posts on the platform. We find some posts from employees with names of Resident Evil characters :D.
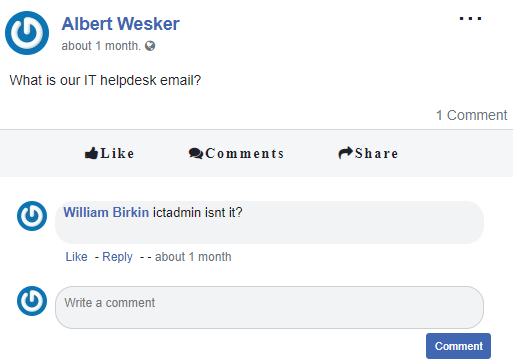
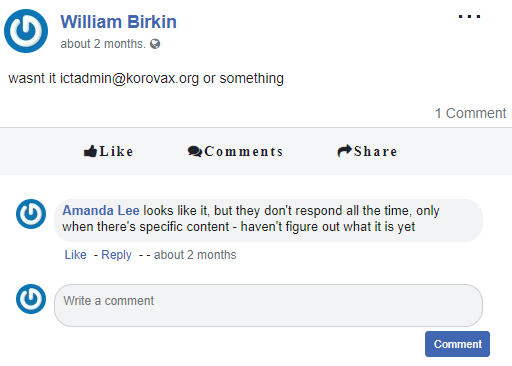
Ah, so we have the e-mail address that we might need to supposedly contact for this challenge. However, based on what Amanda Lee says, we probably need to include specific content in this email before it will reply with the answer.
Indeed, if we send an empty email to the address to verify this, it replies telling us to try again and that it is “missing something”.
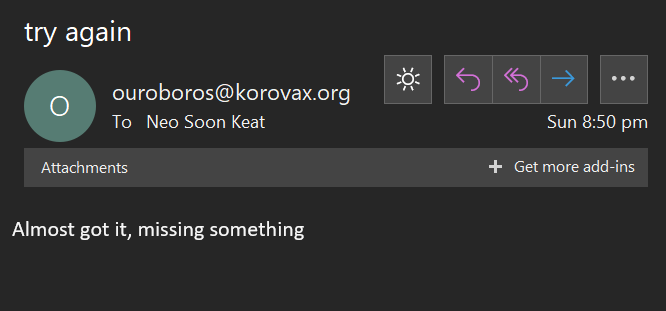
Maybe we can get this specific phrase from the website. Unfortunately, this is a really really specific phrase that we can get from this page of the website (learnt via the sitemap). We can try with the phrase “IT”, since it was bolded and probably means it is very important but it turns out not to be. Realise that the page is called “Never Gonna”, and it is probably a reference to Rick Astley’s 1987 hit “Never Gonna Give You Up”. Realise that the text on the website form the anagram “RICKROLL”. Great. Let’s fire off an email to ictadmin with this anagram now, and we get the response with a flag… Great.
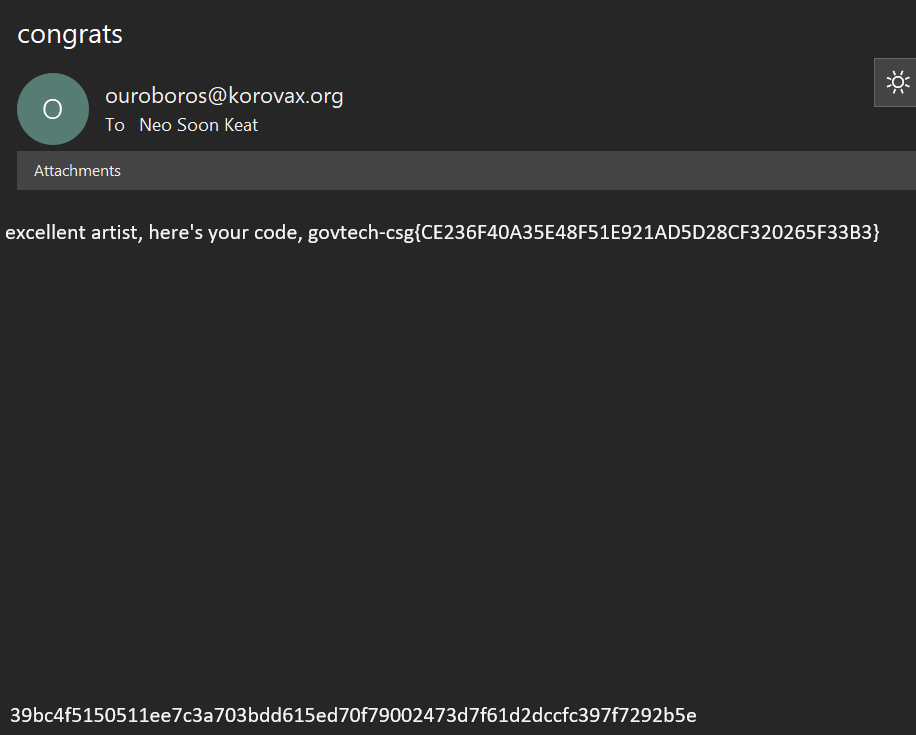
Flag: govtech-csg{CE236F40A35E48F51E921AD5D28CF320265F33B3}
Se-challenge-2: Find the last seen location of where one of the Korovax’s staff is at.
| DESCRIPTION
The evil organisation ‘KoroVax’ has a self help chatbot for new joiners or normal employees to know more about their own organisation. Use this chatbot to ask question and find out more about information about the organisation. Try to get information out of the chatbot! |
Notice that there is a string of alphanumeric characters at the bottom of the email from the previous challenge. This is a SHA256 string. We also know from the internal social media page that there is a Telegram bot. Perhaps that is the chatbot this challenge refers to.
SHA256 is computationally expensive to crack. However, it is possibly already in one of the online lookup tables. We find that it is so, on the website md5decrypt.net.
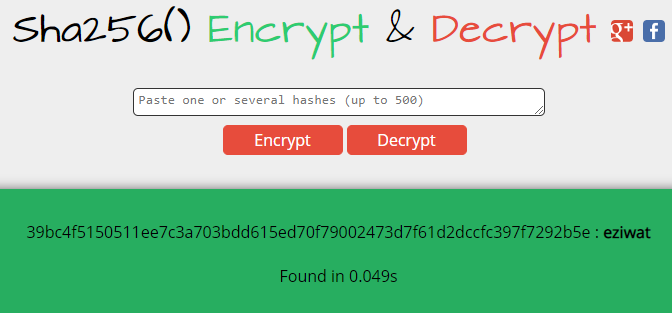
By looking up “eziwat” on Telegram, we come across the bot with the name DAViD! Probably what we’re looking for.
There is a list of exposed functions, however, it is also possible to have commands that aren’t exposed but that the bot responds to. It appears that David can teach us “how to build a botnet”. Maybe we’ll ask it to help us build one then.
With the keyword “/build”, we get through the flow until it eventually gives us the flag! [Pretty sure there are quite a lot of other keywords that the bot would accept too for the same result.]
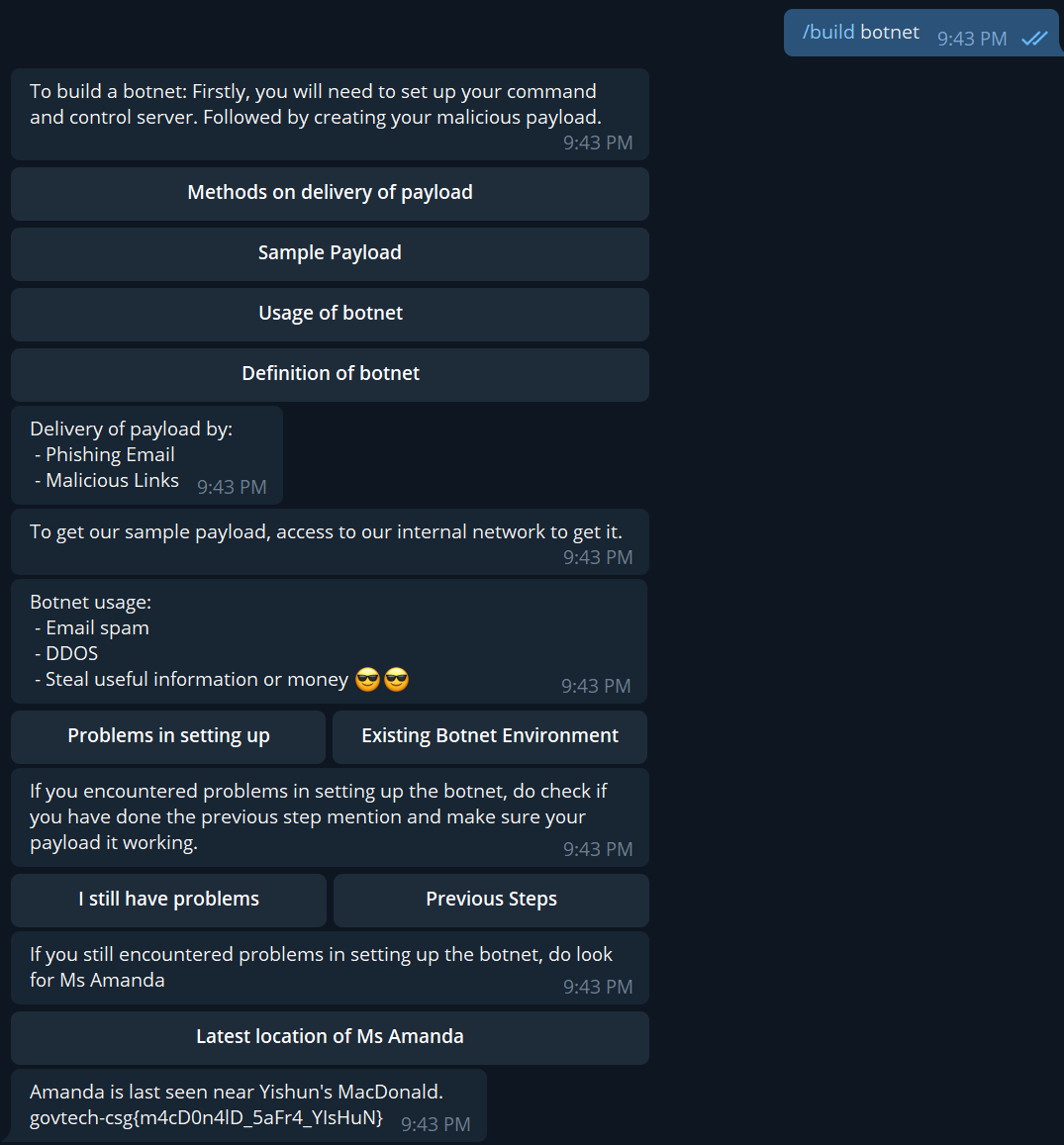
Flag: govtech-csg{m4cD0n4lD_5aFr4_YIsHuN}
Osint-challenge-4: Treasure Media
| DESCRIPTION
Find out more information about the kidnapper. Psst, social media accounts are full of treasures… Find out where she is hiding! The flag format is govtech-csg{latitude,longitude}. Example Flag: govtech-csg{1.352083,103.819839} |
Over the course of investigation, we find references to a handle “@amanda.lee” and “@amanda.hidden” through the posts on the internal social media site, as well as on the KoroVax website.
While “@amanda.lee” does not reveal much information, we see that “@amanda.hidden” has an Instagram profile set up.
The first two posts on the Instagram profile are curious indeed, especially with the comments:
- On the first post at Punggol, it states “Too far away. Seems like it shall be the greens.”
- On the second post at Yishun Town Garden, it states “Greens, looks ideal”.
Looks like we have information on our kidnapper, and that she probably kidnapped to Yishun Town Garden. Now, the question to solve is how to find the latitude and longitude?
For the astute who may have tried, the coordinates on both Google Maps and OneMap don’t work unfortunately. Unfortunately, this was super specific and we had to take the address of Yishun Town Garden – “399 Yishun Ave 2, Singapore 769094” and input it into LatLong.net to get the actual latitude and longitude intended for the challenge.
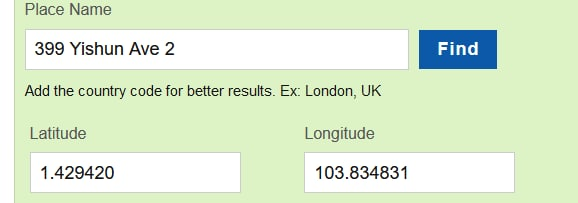
Flag: govtech-csg{1.429420,103.834831}
forensics-challenge-2: Voices in the head
| DESCRIPTION
We found a voice recording in one of the forensic images but we have no clue what’s the voice recording about. Are you able to help? Hint: Xiao wants to help. Will you let him help you? |
We are given a .wav voice recording file. We can analyse the spectrogram in the .wav file using Sonic Visualiser and get a string encoded in base64:

Once the string is decoded, it links to a Pastebin file with a bunch of interesting characters. This is actually a language called “Brainfuck”. We can put it into one of the online interpreters and get the string “thisisnottheflag”.
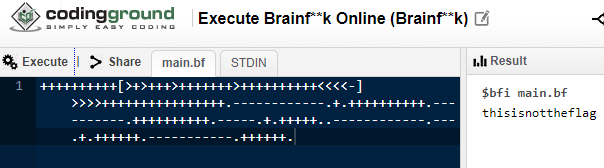
But wait… there’s more. The hint says that Xiao wants to help us. There is a steganography program called “Xiao Steganography” that can hide information within files. Perhaps that’s what this is referring to.
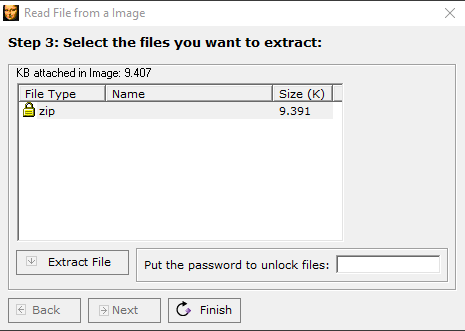
Xiao is asking for a password. Maybe if we use thisisnottheflag…
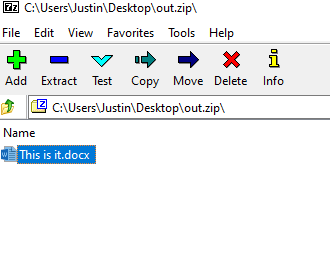
We get “govtech-csg{Th1sisn0ty3tthefl@g}”. Sneaky. Let’s try again.
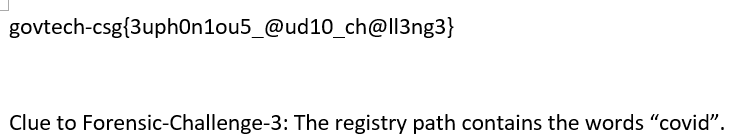
Flag: govtech-csg{3uph0n1ou5_@ud10_ch@ll3ng3}
Iot-challenge-2: COVID’s Communication Technology!
| DESCRIPTION
We heard a rumor that COVID was leveraging that smart city’s ‘light’ technology for communication. Find out in detail on the technology and what is being transmitted. |
The file appears to be a capture of the frames that were transmitted wirelessly at the time. However, this approach uses a non-Wireshark/tshark solution to solve the problem and ONLY uses strings.
Firstly, we look at possible points in the file that could contain interesting data by doing some basic filtering:

We notice that there is a base64 string in there with a partial flag once decoded. The file also includes several other strings like SSIDs and other information typically in beacons. Let us filter it down a bit more and see what we get…
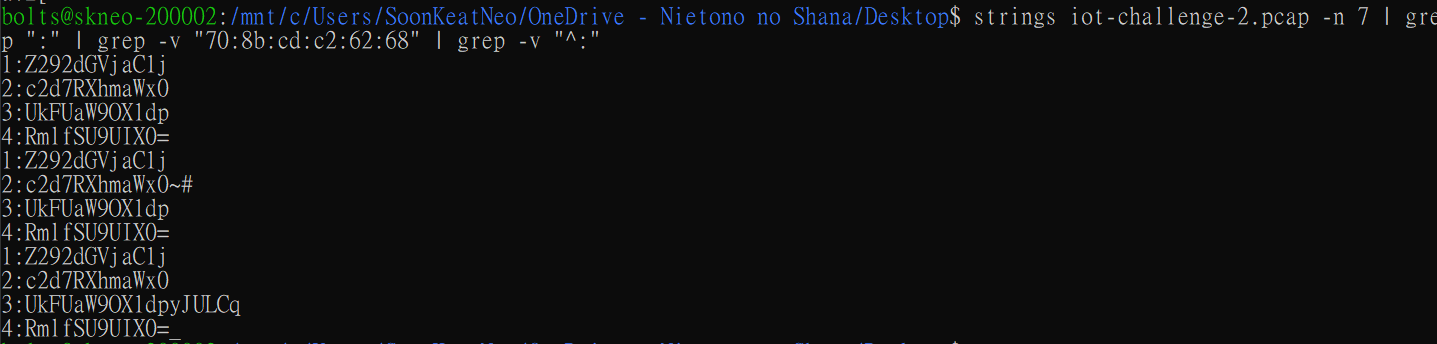
Aha! Looks like a series of strings that could be put together to make up the flag. And if we do so on CyberChef… we get the flag!

Flag: govtech-csg{ExfiltRATioN_WiFi_IOT!}
Misc-challenge-7: Where’s the flag?
| DESCRIPTION
There’s plenty of space to hide flags in our spacious office. Let’s see if you can find it! |
This is a steganography one…
We run pngcheck on the provided PNG file and find that it is malformed. Very sus.

Running strings through the file and converting the base64 reveals a separate image:

Lastly, using StegSolve to change the colour layers reveals the flag on the pole:
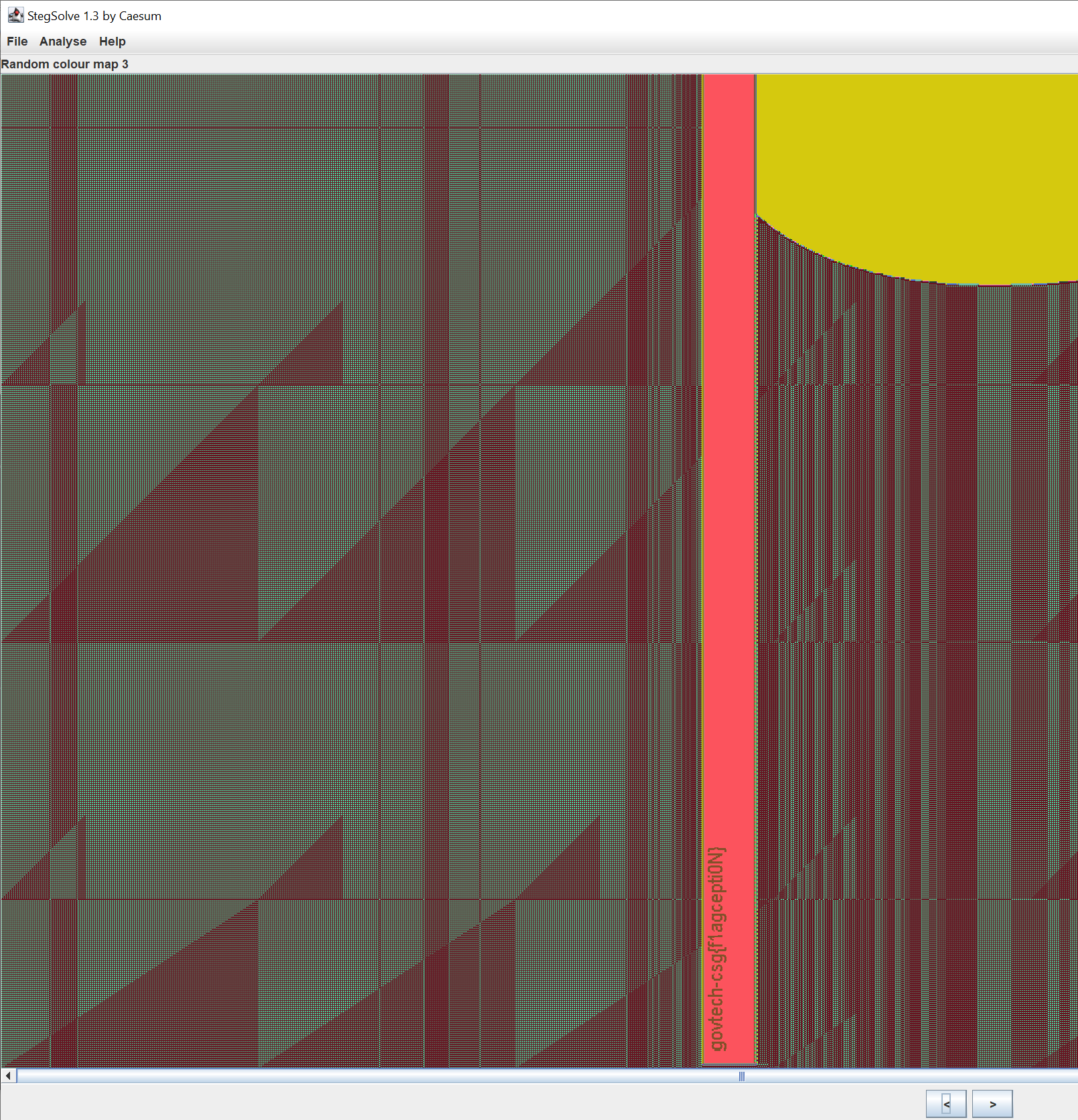
Flag: govtech-csg{f1agcepti0N}